By Lisa Gilbert

By now you probably know that when you get an e-mail from the Prince of Nigeria wanting to share his inheritance with you, or an e-mail notifying you that you won a lottery you didn’t enter, it’s probably not legitimate. But what about that notification that you missed a UPS delivery, or that you need to update your Amazon account because your credit card was declined? All of these are common Phishing scams. The term “Phishing” is a play on “fishing”, and it alludes to the fact that in many cases, the bad actor is angling for valuable information.
You can recognize a phishing email several ways. Most obviously, it will ask you to click on a link or open an attachment. It may be from a sender you recognize, because their e-mail address has been compromised, but you should be able to recognize that it doesn’t look like an e-mai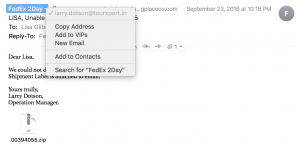 l that person would send. Trust your gut. You can hover your cursor over the sender’s email address, and it will show you the actual email address the message originated from. In a phishing email, it’s common for the real address not to match the displayed address. Here’s an example I received of a missed delivery from “FedEx”.
l that person would send. Trust your gut. You can hover your cursor over the sender’s email address, and it will show you the actual email address the message originated from. In a phishing email, it’s common for the real address not to match the displayed address. Here’s an example I received of a missed delivery from “FedEx”.
Phishing attacks have three common goals: 1. Steal information. 2. Install ransomware. 3. Spread a botnet. The first type will ask you to click a link in the e-mail, which will redirect you to a bogus website that looks a lot like your bank’s website, your Amazon account, or some similar account. When you “log in”, it will steal your credentials (username and password), and use those to attack that account. If you use the same password for several different sites, the attacker may target those sites, as well. The second type will ask you to click on either a link in an e-mail or an attachment to the e-mail, and it will install ransomware on your computer. (If you don’t know what ransomware is and how to protect yourself from it, read my last blog.) You do not want ransomware. It’s very bad. The third type will ask you to click a link or an attachment to the email, and it will install a “bot” on your computer. This is something you will likely never notice, as the purpose is for the bad actor to use your computer resources to attack someone else, usually with the purpose of bombarding a website with traffic to overload it so it can’t be used.
Hopefully, you have recognized a pattern. The phishing email always asks you to CLICK. Click the link, click the attachment — but click. For the love of all that is good, DON’T CLICK. If you think the email may be legitimate and you want to see if your Amazon account is messed up, still don’t click the link. Enter the web address for Amazon directly in your search bar. If you absolutely must see the “attached invoice” or whatever else is purported to be attached to your email, respond to the sender, “I don’t open attachments. Please send the text of the document within your email message.” I have never gotten a response back. Don’t let your curiosity make you open Pandora’s Box – it is likely to be very hard or impossible (or expensive) to close. Just don’t click.
In my next blog, I will be sharing some interesting information on why our biology is working against us and our brains are so willing let us be hacked.


Recent Comments